Multi-factor authentication (MFA) has quickly become a superhero for cybersecurity. MFA allows you to protect your business by requiring at least one additional security identifier on top of your username and password in order to get access to an online account or application.
Though deceptively simple, multi-factor authentication is also shockingly effective. In this article, we delve into why it’s needed, what the MFA process looks like, and ways to incorporate it into your business.
Why is multi-factor authentication needed?
There’s a reason multi-factor authentication has become standard practice for many businesses. “Based on our studies,” said Microsoft’s Alex Weinert, Group Program Manager for Identity Security and Protection, “your account is more than 99.9% less likely to be compromised if you use MFA.”
Put another way: multi-factor authentication protects you from nearly 100% of account hacks.
Passwords, no matter how complex, simply do not provide enough security for your business. Microsoft cloud services see 300 million fraudulent sign-in attempts every day and those passwords are often cracked. As we’ve discussed in our blog on steps to stay secure in the cloud, hackers have an incredible set of tools today to get and get past your password. One way is just sheer brute force and guessing guessing guessing until they’ve got it right. One hacker, for example, developed a program that could try 350 billion guesses a second to crack any 8-character password.
“When it comes to composition and length, your password (mostly) doesn’t matter,” asserts Microsoft’s Weinert.
MFA blocks nearly 100% of account hacks
SOURCE: Microsoft
Then there’s phishing where the hacker tricks you into giving up your password. Of course there are other criminals who simply buy your password on the dark web after any number of data breaches. In fact, the 2020 report From Exposure to Takeover from Digital Shadows Photon Research revealed that cybercriminals already have more than 15 billion stolen credentials.
Another problem with password-only security is that one password can often give a hacker access to more than one account and an awful lot of information. Let’s just take Google as an example. One password can access:
- Calendars
- YouTube
- Web apps, such as Hootsuite (social media) and Salesforce (customer relationship management)
- Any other account where Google is the method chosen for login
Now consider your business. If you’re only using a password to keep your network secure, hackers could theoretically access your financial accounts, confidential company information, health care records, and more. Multi-factor authentication makes stealing your data extremely difficult, which also makes it unlikely that hackers will even try.
What are the “factors” in multi-factor authentication?
There are three elements of multi-factor authentication:
- Something you have Such as a mobile phone
- Something you know Such as a username and password
- Something you are Such as your fingerprint
Two-factor authentication utilizes the first two items on the list and is still an effective way to protect against many security threats. But as hackers become more sophisticated in their attacks, MFA has evolved to include a third factor. It tends to be biometric data, which is unique to you and nearly impossible for bad actors to replicate.

What does the MFA process look like?
A typical multi-factor authentication process involves the following:
- Registration You connect a device to the system, such as your mobile phone, and then claim the device as your own
- Login You enter a username and password into the secure system
- Verification The system connects to the registered device; phones, for example, might ping with a verification code or present a button to click
- Reaction You complete the process with the verified device by entering the code you received or clicking on the button (there is usually a time limit for completing this action)
How many businesses currently use multi-factor authentication?
Despite the fact that multi-factor authentication is by far the most effective protection against hackers, unfortunately some companies remain resistant to it. In 2022, the U.S.-based nonprofit Cyber Readiness Institute conducted a global survey of 1,400 small and medium-sized businesses. They found:
- 55% of companies hadn’t set up multi-factor authentication
- Of those that had set up MFA, only 28% required their employees to use it
- Nearly 60% of survey respondents said they hadn’t even discussed MFA with their employees
The reason for the resistance is largely convenience or, more accurately, inconvenience. Multi-factor authentication does involve at least one extra step in the login process and that’s one step too many for some people.
However, as the Wall Street Journal declared, “The inconvenience of multiple login steps pales next to the risk of using only passwords.” And the risk of using only passwords is making your business vulnerable to cyberattacks.
MFA tools to consider
Since multi-factor authentication offers outstanding protection for your network, we share some applications to consider below. The good news is that they are all completely accessible to small businesses. Google, Microsoft, and 2FAS are free. DUO offers a free version. LastPass and Authy offer free trials. And even if you do select a paid plan, they are affordable. DUO, for example, starts at $3 per user per month.
DUO Security (by Cisco)
MFA on Meraki Go
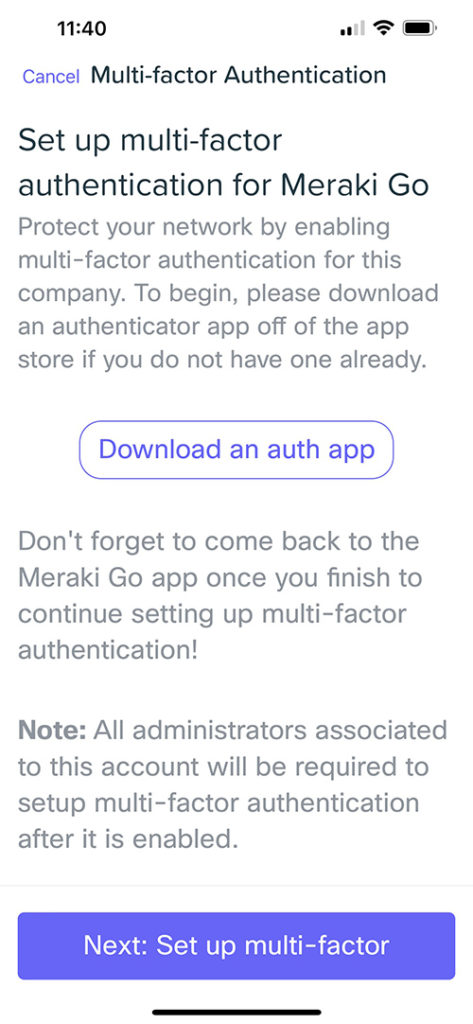
It should be no surprise that Meraki Go offers multi-factor authentication, which protects your networks by adding another security identifier on top of your username and password.
To setup MFA on your Meraki Go account:
- Select the “Settings” tab
- Scroll down to “Account” then select “Multi-factor Authentication”
- Download an authenticator app (like those above)
- Once downloaded, return to Meraki Go and select “Add Meraki Go” to add your credentials to the authenticator app
- Return to Meraki Go to verify your one-time password by entering the code
- Select “Enable”
Final thoughts
Don’t be someone who is resistant to multi-factor authentication. To remind you of the threats small businesses face, you can read more on the blog about malware and phishing. You can also hear straight from Cisco’s cybersecurity expert Mike Storm on how small businesses get hacked and why MFA is so important.
Multi-factor authentication is neither difficult nor is it expensive. Though it may feel inconvenient, any additional step MFA requires is a small price to pay for nearly 100% protection against hacks. As PC Mag puts it, “The bad guys count on you being lax.” Don’t be.

SOURCES:
Cyber Readiness Institute
Digital Shadows Photon Research report “From Exposure to Takeover”
DUO
Forbes
Google
Microsoft
Okta
PC Mag
TechRadar
Wall Street Journal
U. S. Cybersecurity and Infrastructure Security Agency
ZD Net





